Trapdoor One Way Function Example

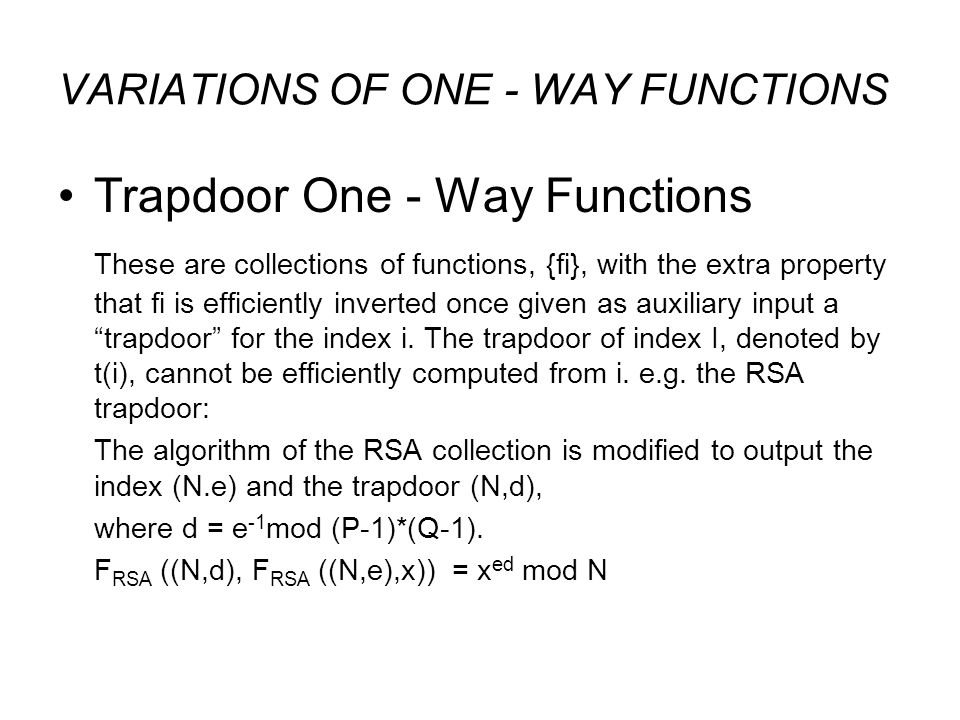
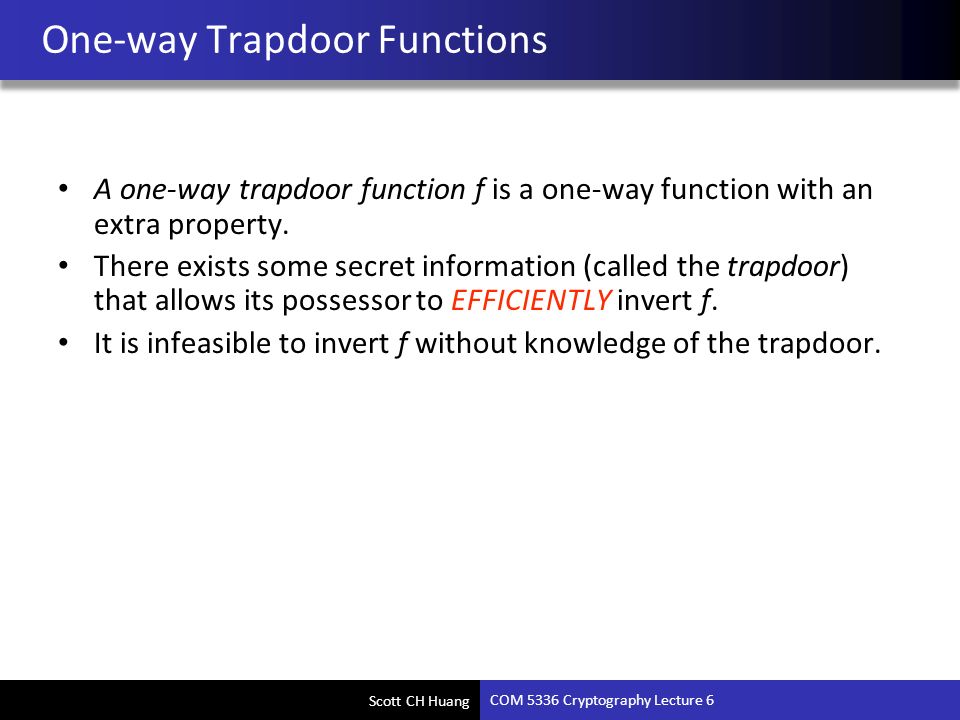
A trapdoor one way function or trapdoor permutation is a special kind of one way function.
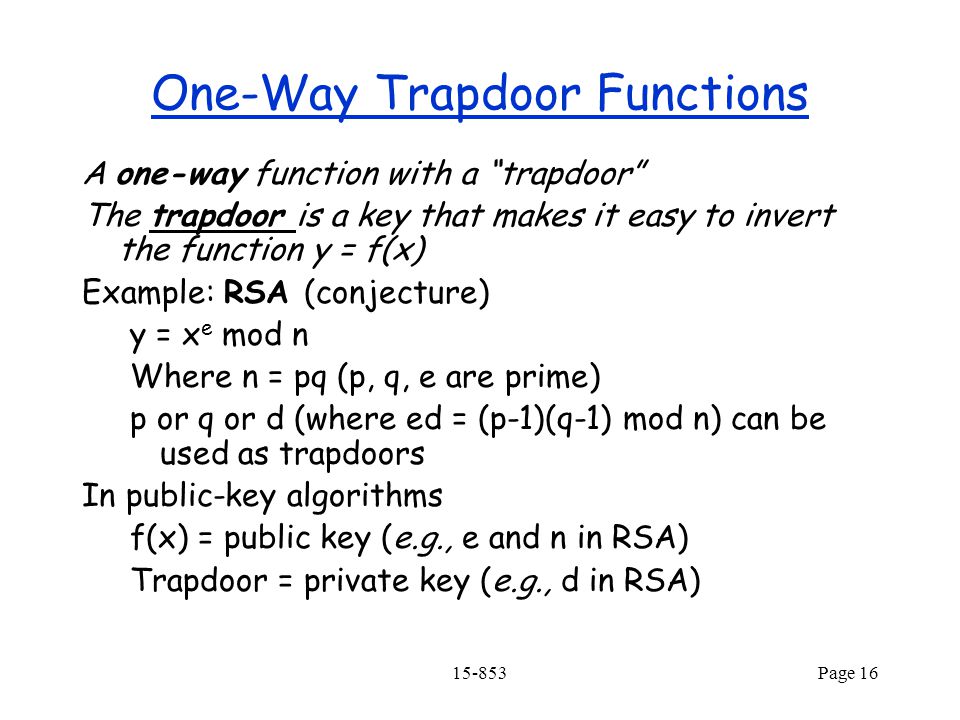
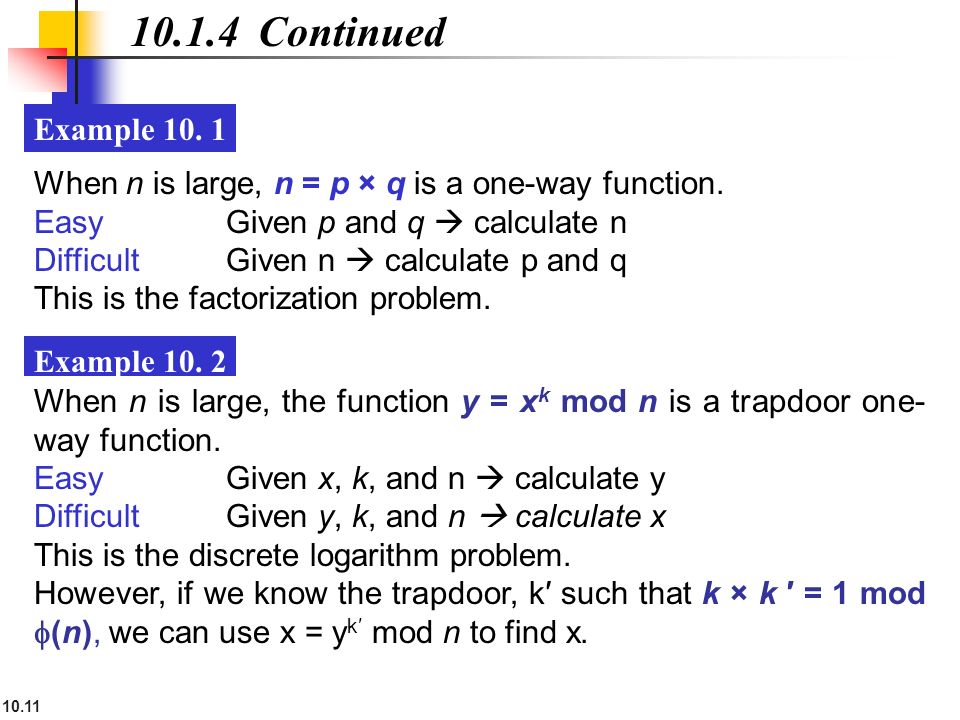
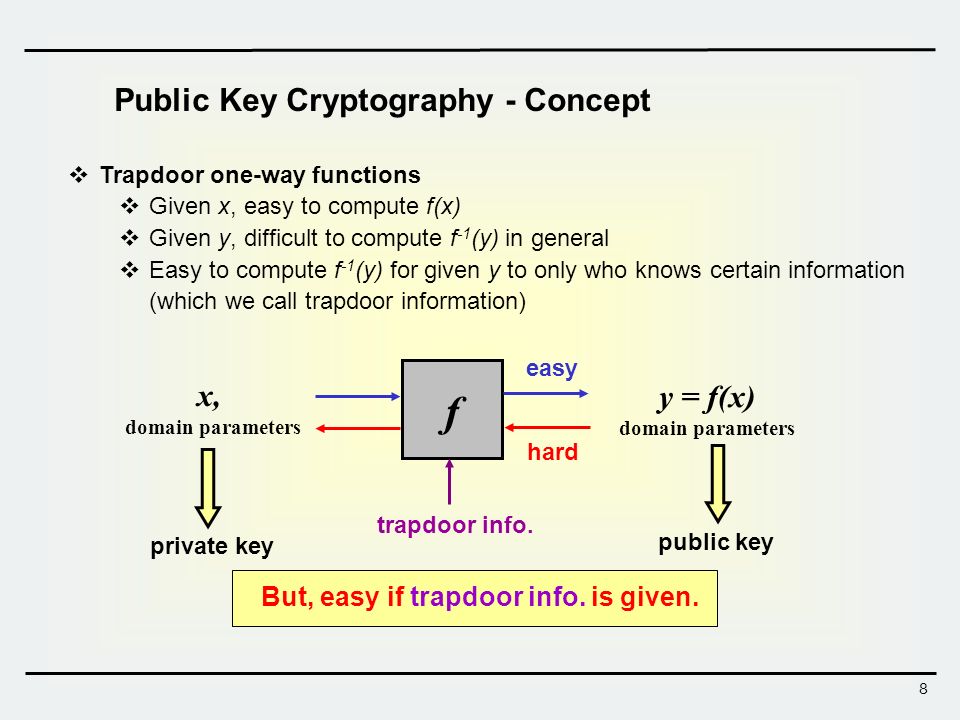
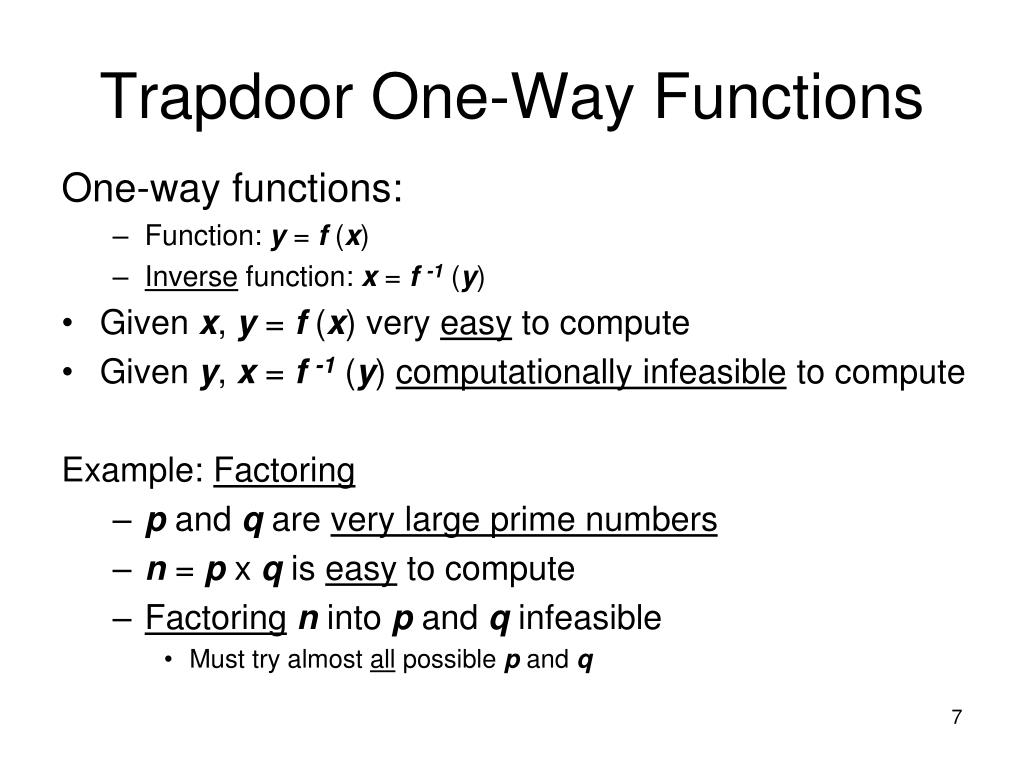
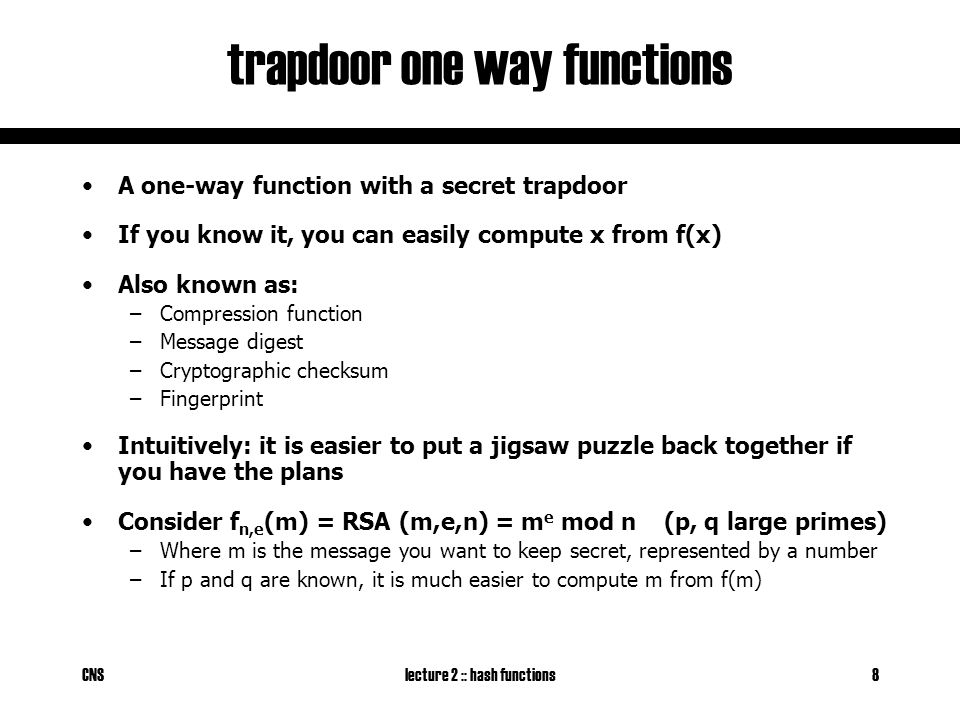
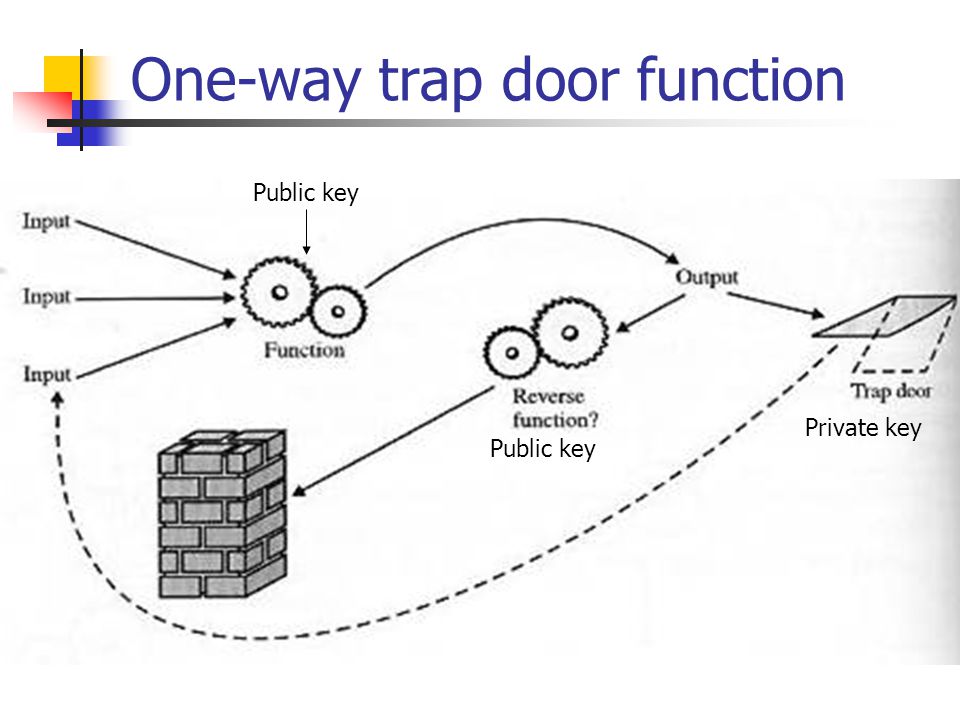
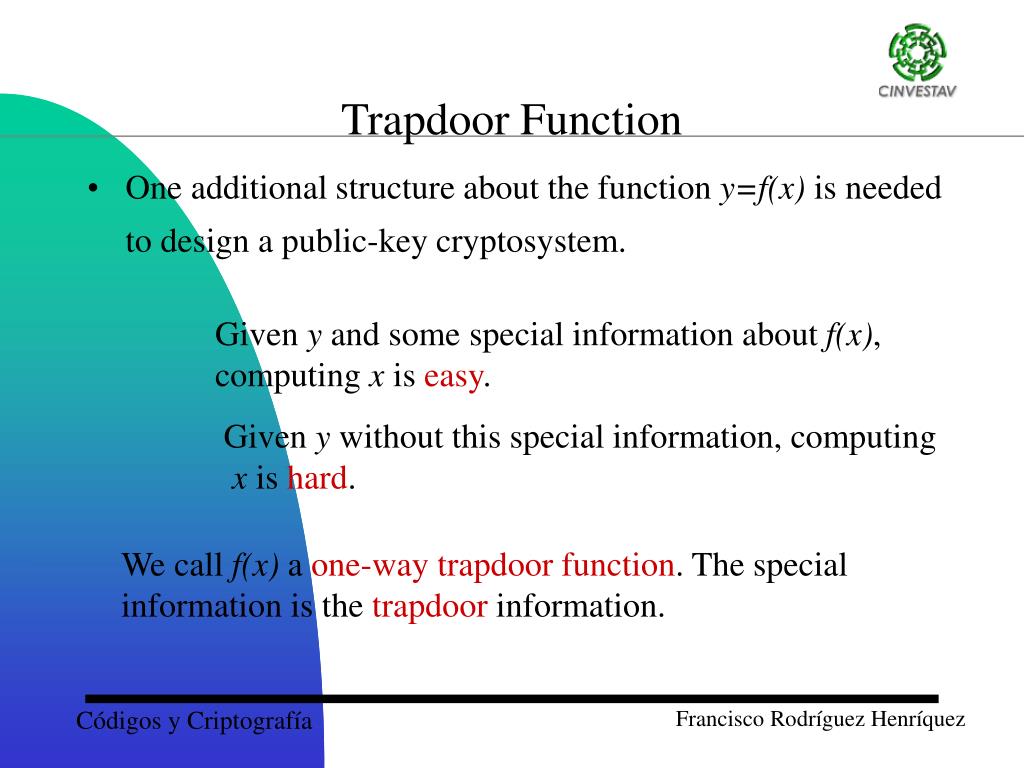
Trapdoor one way function example. For fixed public key is viewed as a function of that maps bits to bits. Not being one to one is not considered sufficient of a function for it to be called one way. A trapdoor one way function is a function that is easy to compute but computationally hard to reverse easy to calculate f x from hard to invert. Nowadays this task is practically infeasible.
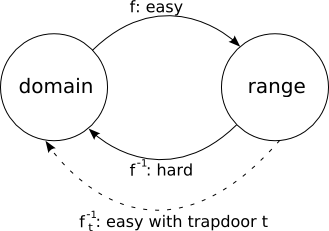
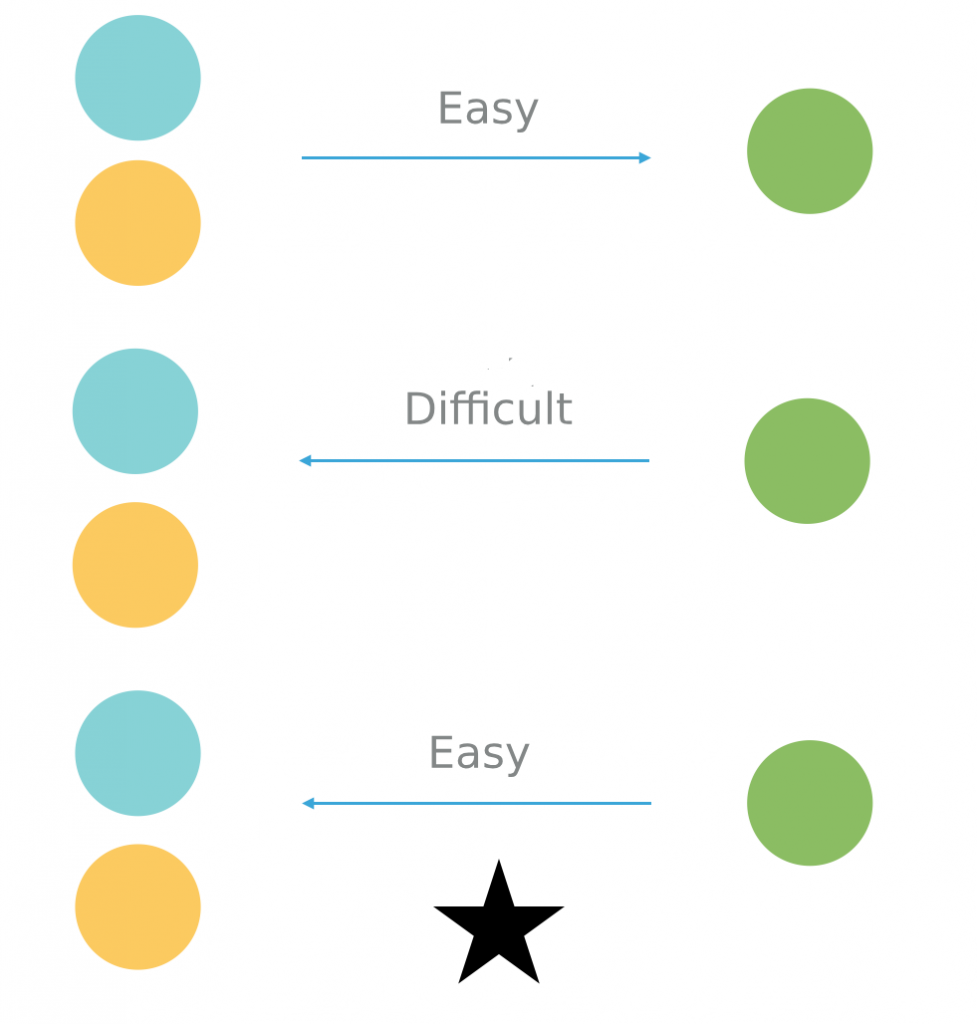
This video gives a motivation and a general idea about the concept of one way function in cryptography. Is a trapdoor one way hash function if is also a one way hash function i e if additionally. Such a function is hard to invert unless some secret information called the trapdoor is known. In mathematical terms if f is a trapdoor function there exists some secret information y such that given f x and y it is easy.
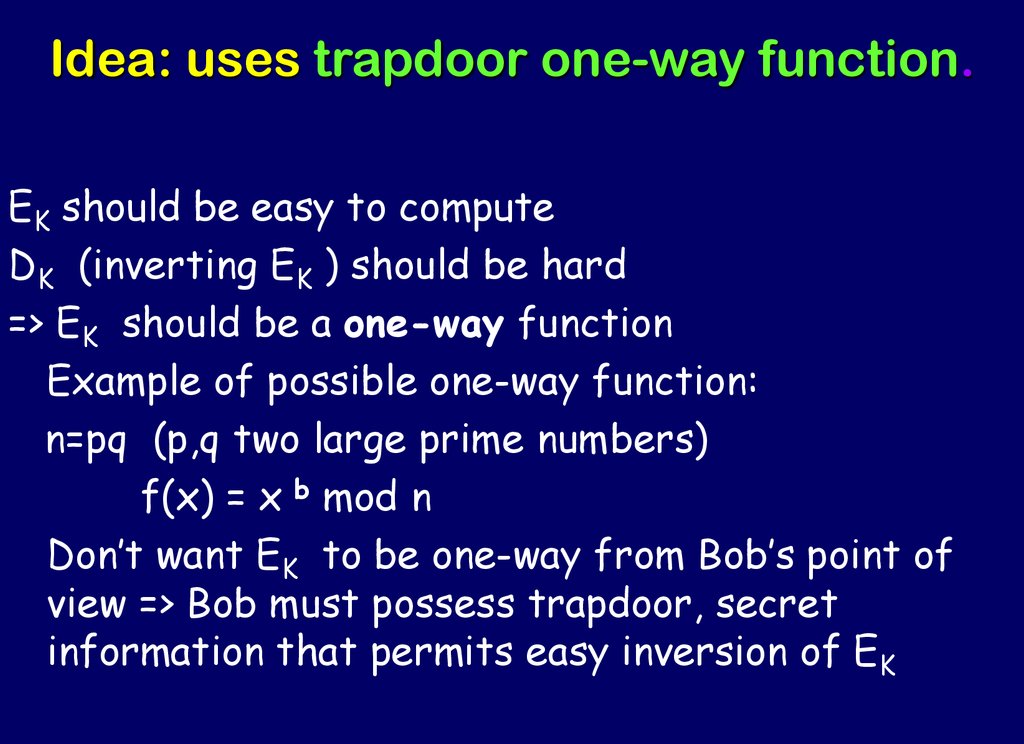
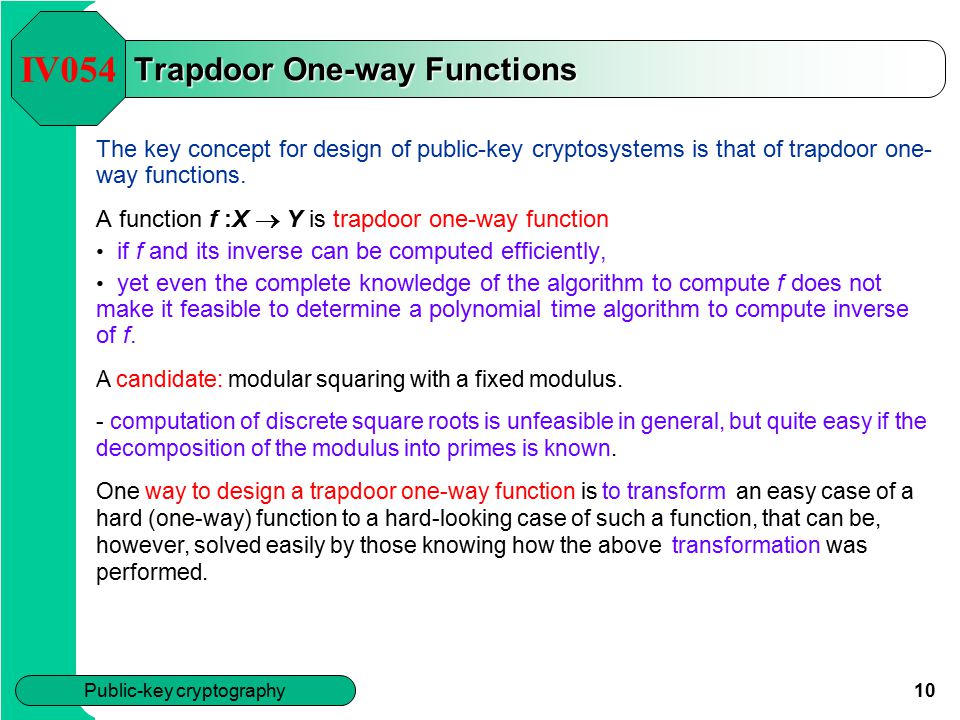
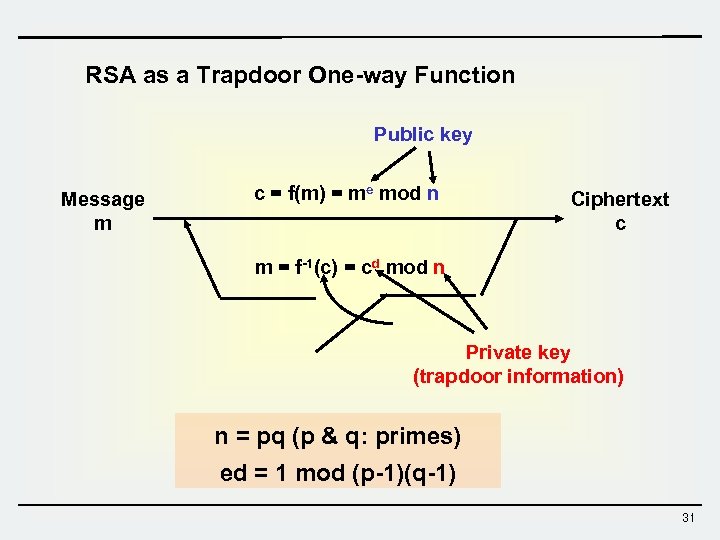
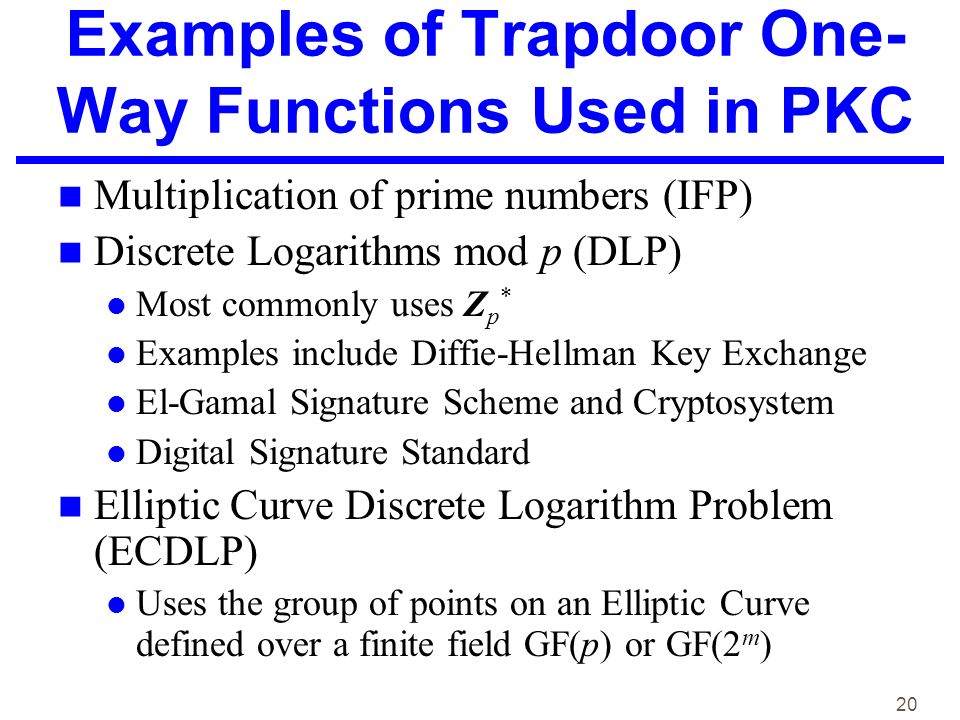
An example of such trapdoor one way functions may be finding the prime factors of large numbers. The concept of function is defined and some example. Then there is an efficient algorithm that on input produces such that for some trapdoor key. A trapdoor function is a function that is easy to compute in one direction yet believed to be difficult to compute in the opposite direction finding its inverse without special information called the trapdoor trapdoor functions are widely used in cryptography.
A collision free hash function f is a one way function that is also collision resistant. A trapdoor function is a function that is easy to compute in one direction yet believed to be difficult to compute in the opposite direction finding its inverse without special information called the trapdoor. Informally a function is a trapdoor one way function if. In mathematical terms if f is a trapdoor function then there exists some secret information t such that given f x and t it is easy to.
A trapdoor function is a function that is easy to compute in one direction yet difficult to compute in the opposite direction finding its inverse without special information called the trapdoor trapdoor functions are widely used in cryptography.