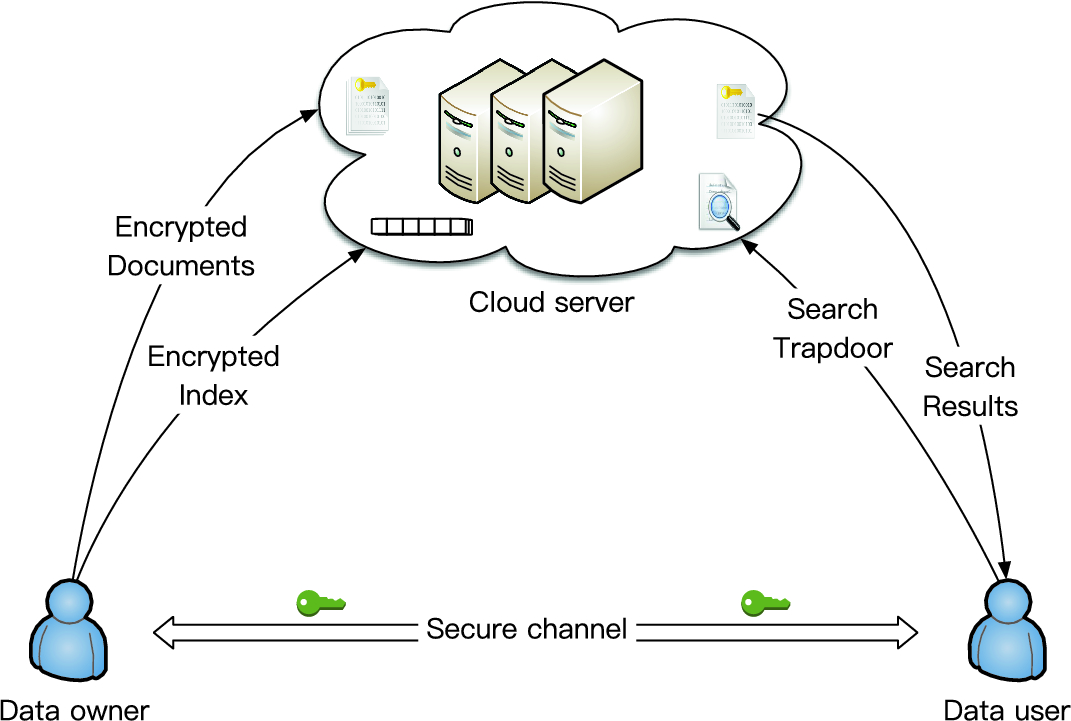
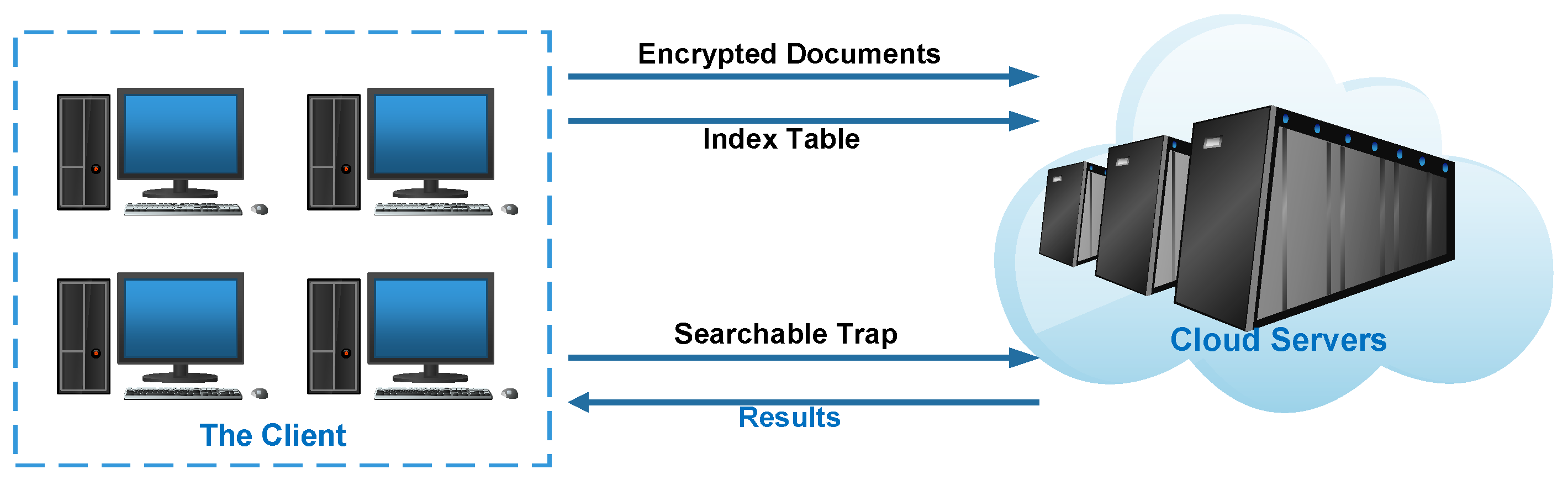
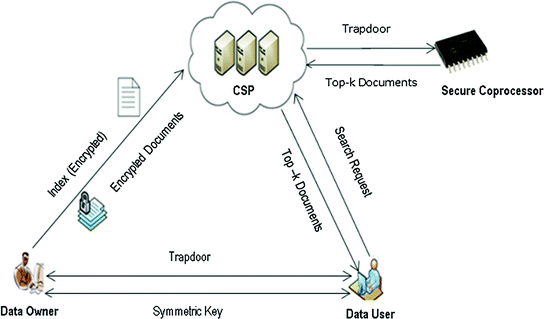
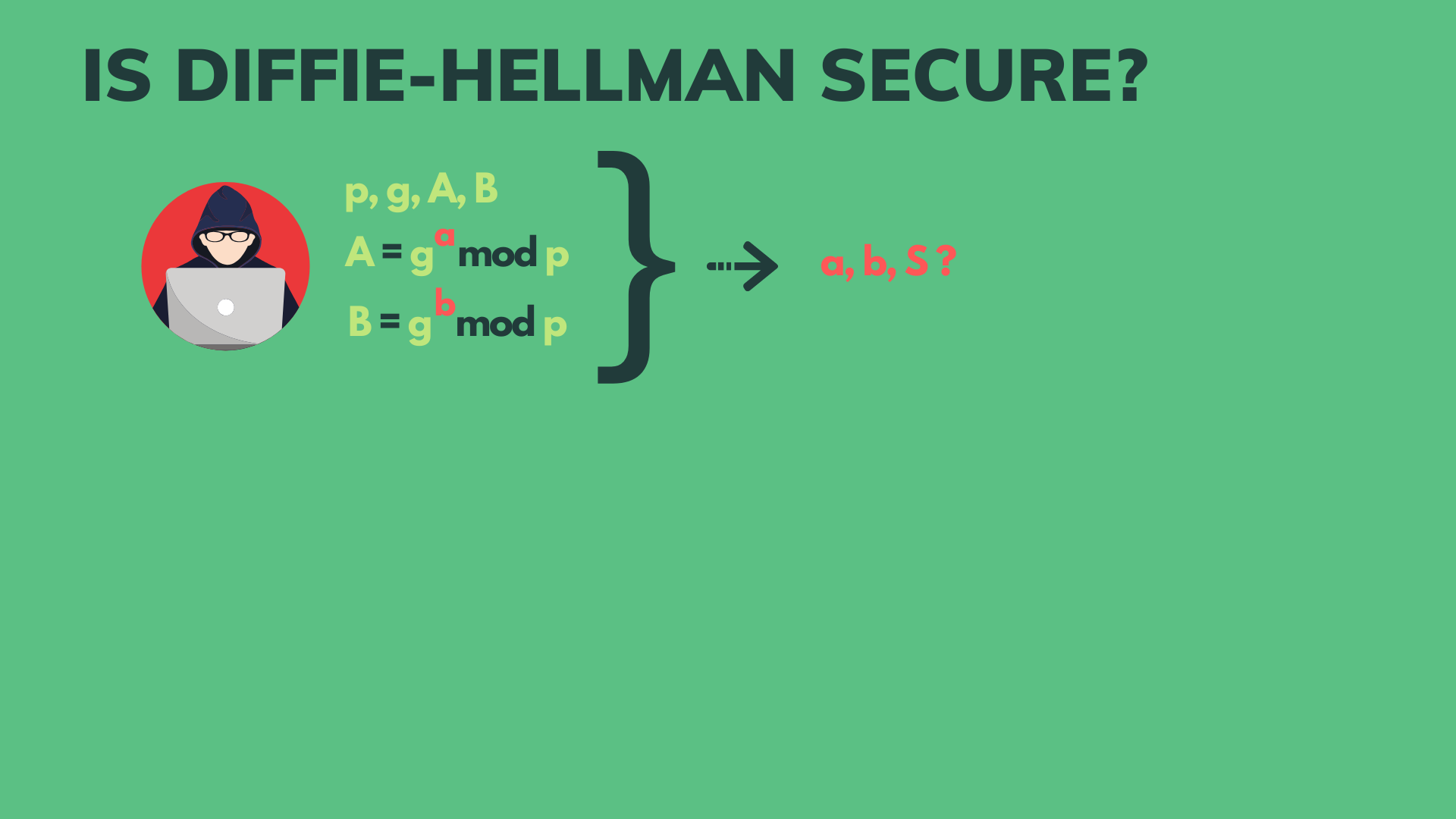
Trapdoor Function Security
Lossy trapdoor functions ltfs introduced by peiker and waters in stoc 08 are functions that may be working in another injective mode or a lossy mode.
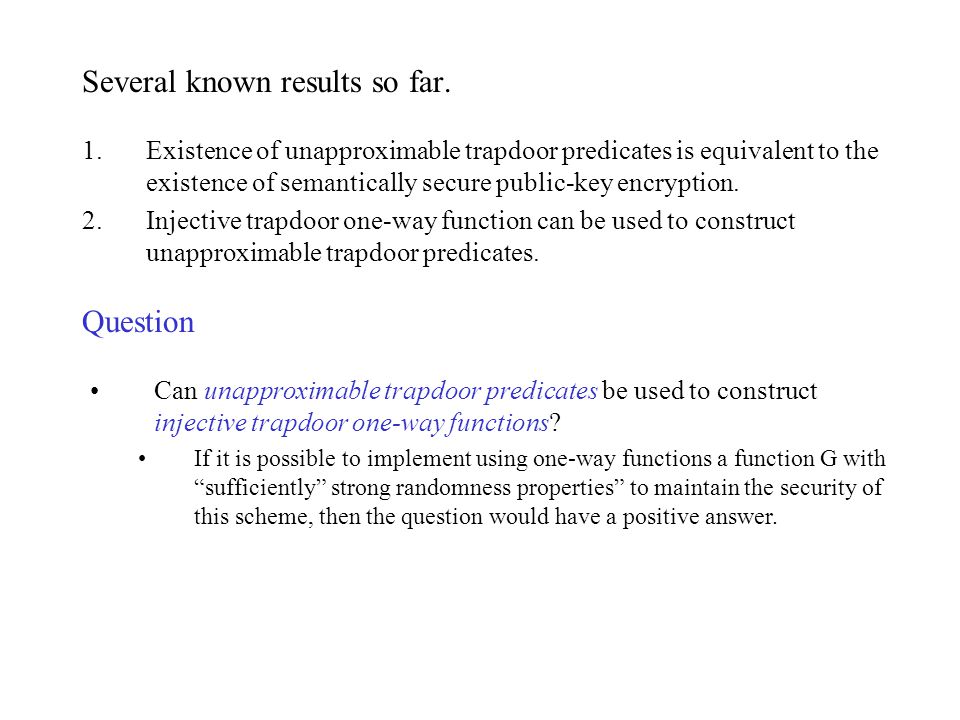
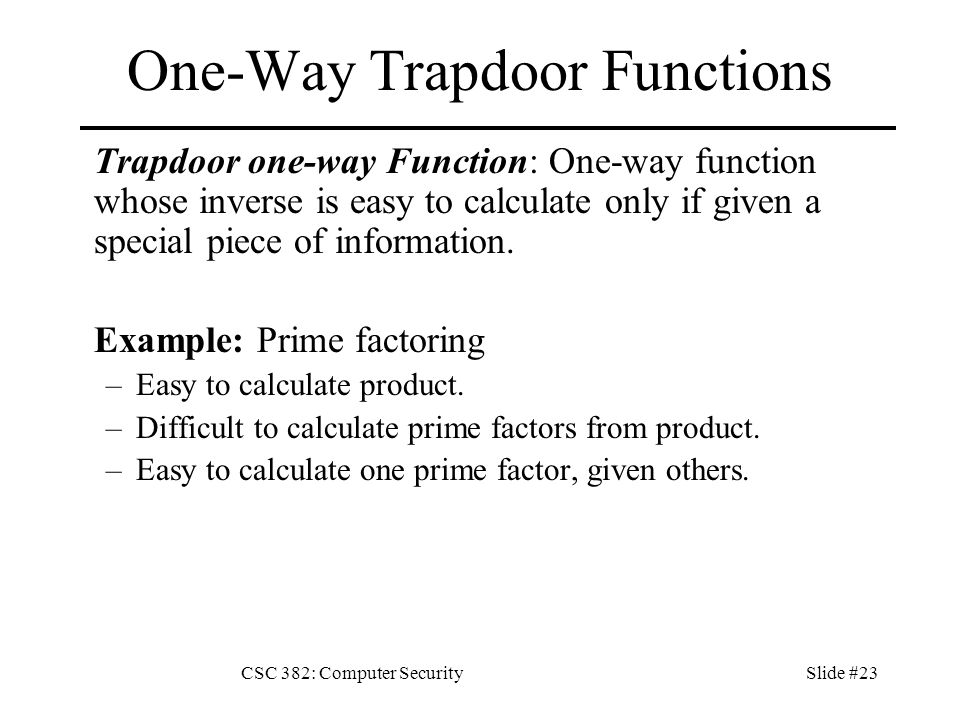
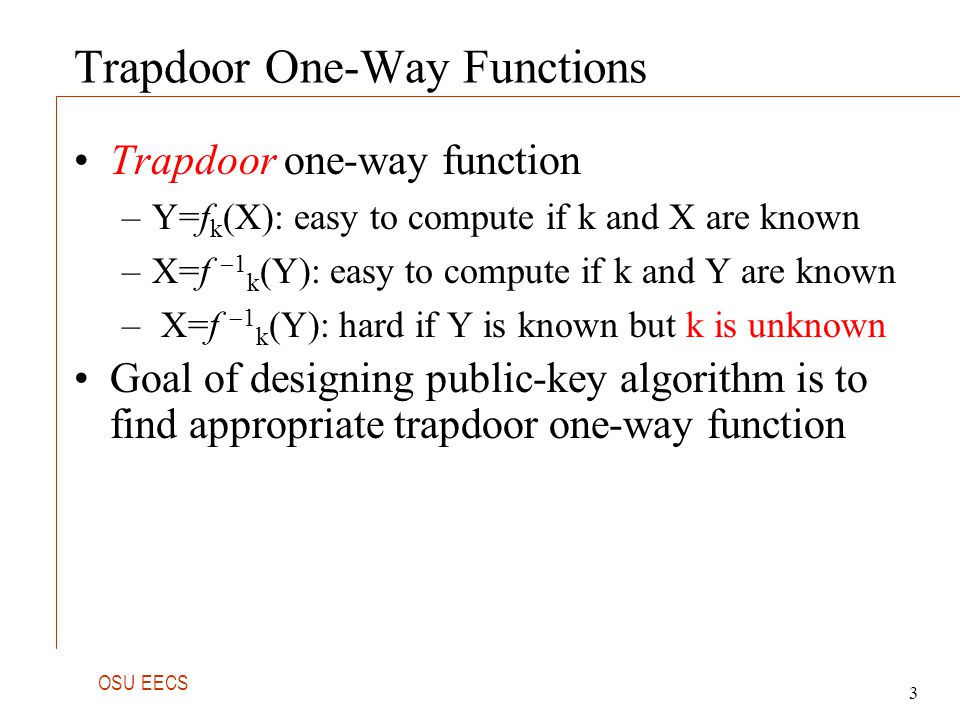
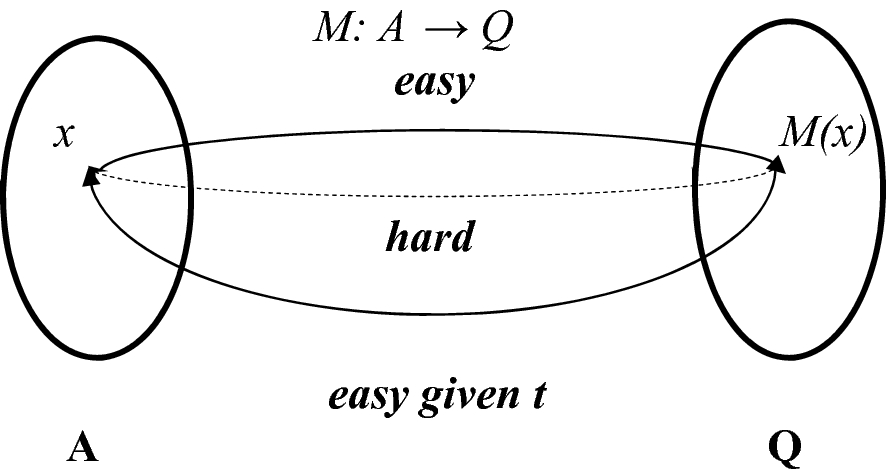
Trapdoor function security. The main building block of our construction is a novel primitive called sampleable range trapdoor function that is a trapdoor. A trapdoor function is a function that is easy to compute in one direction yet believed to be difficult to compute in the opposite direction finding its inverse without special information called the trapdoor trapdoor functions are widely used in cryptography. In mathematical terms if f is a trapdoor function there exists some secret information y such that given f x and y it is easy. Page 13 thm fops 01.
In mathematical terms if f is a trapdoor function then there exists some secret information t such that given f x and t it is easy to. G plaintext to encrypt with rsa reject ct if invalid. A trapdoor function is a function that is easy to compute in one direction yet difficult to compute in the opposite direction finding its inverse without special information called the trapdoor trapdoor functions are widely used in cryptography. This paper studies lossy trapdoor functions with i tight security i.
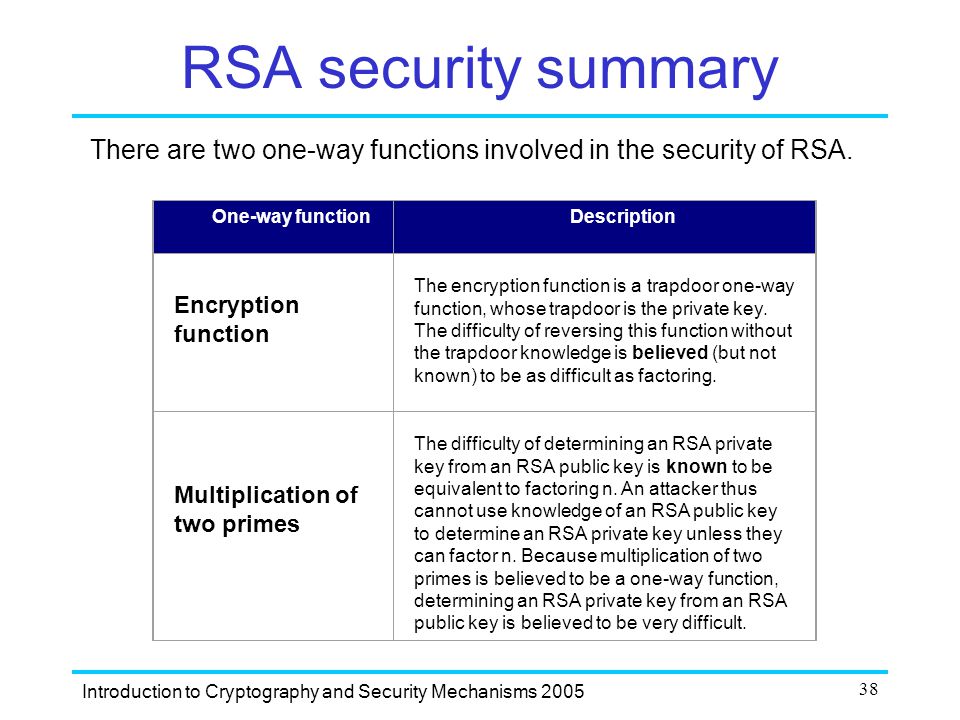
Check pad on decryption. Trapdoor functions which informally are hard to invert unless one possesses some secret trapdoor information conceptually date back to the seminal paper of diffie and hellman 18 and were first realized by the rsa function of rivest shamir and. Use sha 256 for h and g. Trapdoor function i e permutation and doubly enhanced lossy correlated product secure was required and critical for achieving chosen ciphertext security leaving open the problem of building chosen ciphertext secure encryption by only assuming injective trapdoor functions.
Security from trapdoor functions pedro branco manuel goul ao paulo mateus abstract we propose a generic framework for perfectly hiding uc commitment schemes in the global random oracle model of canetti el at. Oaep br94 h m 01 00 0 rand. Similarly it is asked what is trap door in security. Rsa is trap door permutation rsa oaep is ccs when h g are random oracles.
Given such a function key it is impossible to distinguish an injective key from a lossy key for any probabilistic polynomial time adversary. Click to see full answer. Additionally what is backdoor and trapdoor. Moreover the trap door is often activated by an event or a normal action.
The use of the word trapdoor here clearly coincides with more recent definitions of a backdoor. Security under chosen ciphertext attack cca security 39 45 20.